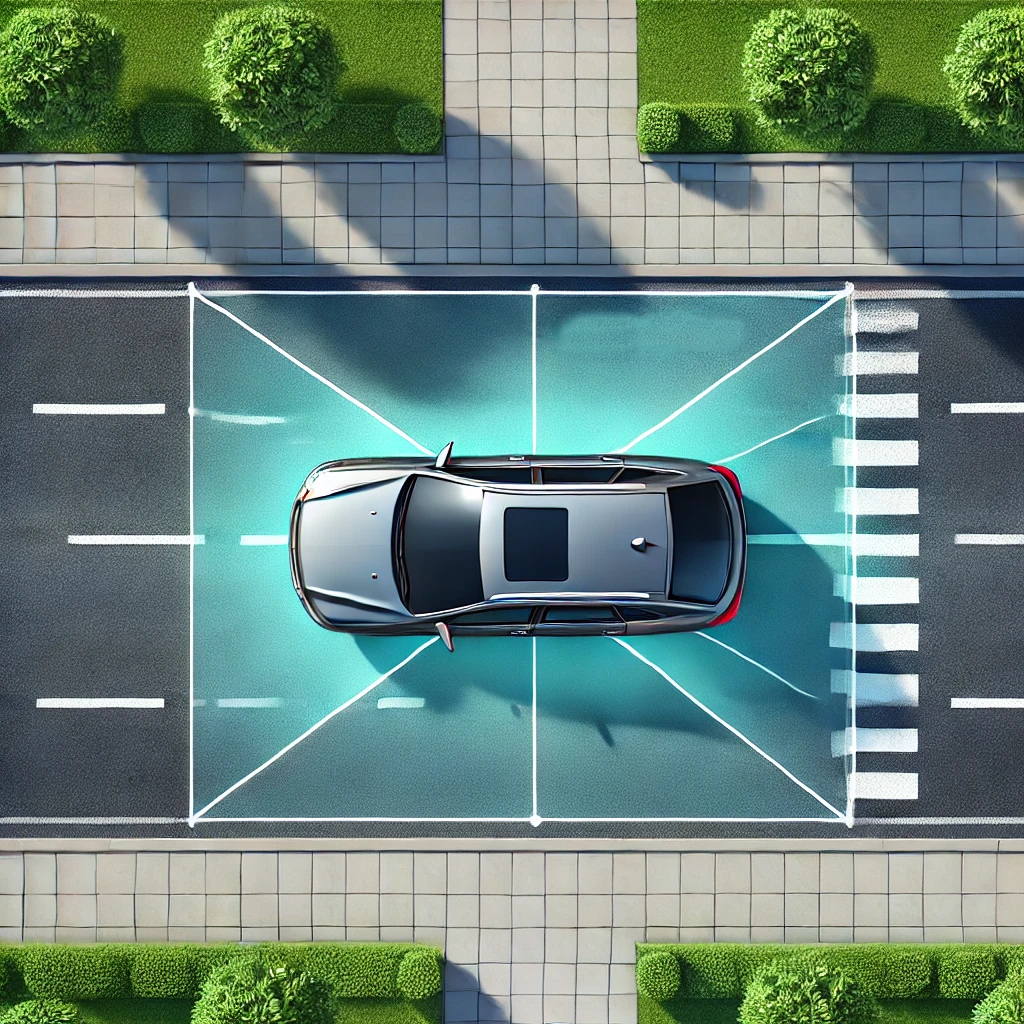
When it comes to personal security and executive protection, a proactive and structured approach is key. One of the most effective strategies used by security professionals is the concept of concentric circles and layered defense. This tool creates multiple levels of protection that mitigate risks before they even reach the intended target.
After introducing this essential security tool, let’s dive deeper into how its principles can be applied to enhance personal safety and executive protection. In the following sections, we’ll explore the foundational concept of concentric circles and the complementary strategy of layered defense.
Concentric Circles in Security
Imagine your personal security as a series of rings encircling you, each representing a distinct level of protection. The outermost circle serves as the first barrier against potential threats, while inner circles offer increasingly refined layers of defense. This structured approach is not only theoretical; it is actively implemented by executive protection teams and security professionals around the world.
The outer perimeter is designed to monitor and control the environment around your immediate location. This may involve scanning for suspicious individuals or vehicles near venues, events, or travel routes. For personal security, it translates to being vigilant about your neighborhood or workplace. Trusted organizations like the U.S. Department of Homeland Security emphasize environmental awareness as a first step in risk mitigation.
Moving inward, the middle perimeter focuses on limiting access to spaces where you are most vulnerable, such as your home, office, or vehicle. This level includes physical barriers like fences, security systems, and controlled entry points. Executive protection teams often secure these areas through surveillance and checkpoints. Incorporating cyber monitoring into this layer ensures that unauthorized digital intrusions are also prevented, as highlighted by cybersecurity resources on the FBI’s cyber division website.
The innermost circle is the final line of defense. It represents the immediate security around you—this might include personal bodyguards, alert systems, or even specialized protective gear like bulletproof clothing and armored vehicles. This layer is designed to protect you in scenarios where outer defenses have been breached, ensuring a rapid and effective response to any threat.
Integrating Layered Defense for Strength in Depth
Layered defense works in tandem with the concentric circles model to ensure that if one protective layer is compromised, the next one is ready to mitigate or neutralize the threat. This concept, known as “defense in depth,” relies on multiple strategies that work cohesively to safeguard individuals.
Physical barriers, such as gates, locks, and fences, are the most tangible elements of layered defense. They serve to slow down or deter potential intruders long before they reach your inner circles. These measures are often the first line of defense and are crucial in creating a secure perimeter around any property or individual.
Security personnel are another critical component. Whether in the form of bodyguards, security officers, or specially trained professionals, these individuals provide active surveillance and the ability to intervene in potentially dangerous situations. Their presence alone can often discourage adversaries from attempting to breach any level of defense.
Technological enhancements such as alarms, cameras, and motion sensors add yet another layer of vigilance. These systems not only detect unusual activity but also provide real-time alerts that allow for swift responses. For additional insights into technological security measures, refer to resources available through Security Magazine.
Situational awareness is perhaps the most dynamic element of layered defense. It involves being mentally and physically alert to the surroundings, understanding what is normal, and recognizing anomalies that could signal a threat. This heightened awareness enables you to respond quickly and effectively to changes in your environment. Trusted institutions like NATO emphasize the importance of situational awareness in both military and civilian security practices.
Protective intelligence plays a crucial role as well. This involves gathering and analyzing information about potential threats in your area. By staying informed about current crime trends, local disturbances, or emerging hazards, you can proactively adjust your security measures. Many security firms incorporate intelligence data to tailor their protection strategies, ensuring that every layer of defense is up-to-date with the latest threat information.
Finally, behaviors and actions contribute significantly to your overall security. How you act and react—choosing safe routes, dressing inconspicuously, and remaining alert to your surroundings—can reduce your risk profile substantially. Even the most sophisticated security systems can be undermined by careless behavior. This is why many professional security advisors recommend regular training and drills to reinforce safe practices.
Why Concentric Circles and Layered Defense Matter
The combination of concentric circles and layered defense provides a systematic approach to managing risks. By breaking down protection into distinct, manageable layers, each with its own function and response capability, the overall security framework becomes robust and resilient.
For personal security, this method ensures that even if an adversary manages to breach one layer, subsequent layers are in place to prevent further escalation. In the realm of executive protection, where the stakes are significantly higher, such a structured approach is indispensable. It allows security teams to create a buffer zone around high-profile individuals, ensuring that threats are neutralized well before they reach their target.
This layered approach also buys valuable time for emergency responses. In situations where an attack is imminent, each protective layer acts as a time-delay mechanism, giving law enforcement or security personnel the critical moments they need to react. Time is often the most crucial factor in preventing a threat from becoming a full-blown incident.
Moreover, layered defense is adaptable. Whether you are protecting a celebrity, a corporate executive, or yourself, the principles remain the same. By tailoring each layer to specific vulnerabilities and risk factors, you can create a customized security strategy that addresses both physical and digital threats. This adaptability is why security professionals worldwide continue to rely on the concentric circles model.
The concept also fosters a mindset of continuous vigilance. It encourages individuals to think beyond a single point of failure and to implement multiple, overlapping safety measures. This mindset is critical in today’s fast-paced and often unpredictable world, where threats can emerge from unexpected quarters.
Applying the Principles in Real-World Scenarios
Consider a scenario where a high-profile executive is traveling to a large public event. The outer perimeter might involve securing the venue with metal detectors, CCTV cameras, and patrols by security personnel. Meanwhile, the middle perimeter ensures that access to restricted areas—such as backstage zones or private lounges—is controlled and monitored. Finally, the inner perimeter includes the executive’s personal bodyguards, who are trained to react instantly to any signs of danger.
In another instance, think about personal security at home. The outer perimeter might include neighborhood watch programs and external lighting systems that deter criminals. The middle layer could be reinforced by installing high-quality locks, security alarms, and even video doorbells. The inner circle might consist of smart home systems that alert you to any unusual activity, along with a plan for contacting local law enforcement promptly. Such a multi-layered approach significantly reduces the likelihood of an incident escalating into a serious breach.
For those interested in learning more about how layered defense can be implemented, reputable sources like The Security Industry Association provide detailed guidelines and case studies. These resources offer practical insights into how various security measures work together to create a robust defense strategy.
Furthermore, the principles of layered defense are not limited to physical security. In today’s digital age, protecting sensitive information requires a similar approach. Just as with physical security, digital safety is enhanced by multiple layers of protection, such as firewalls, encryption, and multi-factor authentication. By applying the same strategic thinking to both physical and digital realms, you ensure a comprehensive safety net that covers all potential vulnerabilities.
Enhancing Personal Safety with Proactive Strategies
Beyond technology and physical barriers, the true strength of concentric circles and layered defense lies in proactive planning and situational awareness. Regular training sessions, security audits, and drills can help you stay prepared for unexpected events. Whether you are an individual or part of an executive protection team, continuous improvement and adaptation of security measures are vital.
Developing a habit of proactive vigilance means that you are always on the lookout for potential threats. This can include simple practices like reviewing local news reports, monitoring social media for real-time updates, or participating in community safety programs. For instance, the International Association of Professional Security Consultants (IAPSC) provides resources and training that can enhance your ability to detect and respond to security threats effectively.
Moreover, maintaining a secure environment requires ongoing communication among all parties involved. In an organizational setting, regular briefings between security personnel, executive teams, and IT professionals ensure that everyone is aware of the latest threats and the measures in place to counter them. In personal security scenarios, sharing information with trusted family members or colleagues can create an informal network of vigilance that enhances overall safety.
In essence, the integration of concentric circles and layered defense is about building resilience into your security infrastructure. It’s about ensuring that no single failure point can compromise the entire system. By adopting a layered approach, you create multiple redundancies that work together seamlessly to protect you from harm.
Building a Resilient Security Framework
In today’s unpredictable world, relying on a single line of defense is no longer sufficient. The concept of concentric circles and layered defense offers a comprehensive strategy that is both effective and adaptable. Whether you are focused on personal security or tasked with protecting high-profile individuals in an executive capacity, this tool provides a robust framework to mitigate risks and neutralize threats before they escalate.
By understanding and implementing each layer—from the outer perimeter that monitors the broader environment to the inner circle that ensures immediate protection—you are taking significant steps toward enhancing your overall security. Coupled with proactive strategies, continuous training, and reliable intelligence, layered defense not only secures you against immediate threats but also fosters a culture of vigilance and preparedness.
Embracing this approach means accepting that security is a multi-faceted endeavor. It is about combining technology, physical measures, and behavioral strategies into one cohesive system. As you refine your personal or organizational security framework, remember that each layer of defense adds valuable time and resources for a swift response, ultimately keeping you, your colleagues, or your loved ones safe.
For further reading on best practices and emerging trends in security, consider visiting trusted sources like the Security Industry Association or the U.S. Department of Homeland Security. These organizations offer a wealth of information that can help you stay informed and continuously improve your defense strategy.
Ultimately, a well-designed system of concentric circles and layered defense is not just a theoretical model—it is a practical, proven method that enhances both personal security and executive protection. By investing in this tool and committing to a proactive, multi-layered approach, you are better prepared to face any threat and ensure that your safety remains uncompromised.